Hardware Wallet Vs Software Wallet - 5 Crucial Differences
Protect your crypto assets wisely! Discover the ultimate showdown between hardware wallet vs software wallets.
Author:Tyreece BauerReviewer:Anderson PattersonFeb 26, 20244.7K Shares68.2K Views

A wallet is just as necessary in the cryptocurrency world as it is in the real world for storing cash. It is a wallet for storing digital assets rather than cash or conventional money, yet it is made of leather. One can access their digital currency through the wallet, which serves as an interface. The wallet that a person selects will determine the ease of use and security of their digital assets.
One must strike a balance between the two somewhere, and doing so necessitates taking many things into account. There are two main types of bitcoin wallets - hardware wallet and software wallet, each with a different design philosophy. This article explains the main distinctions between hardware and software wallets along with a number of criteria and a few instances.
5 Comparisons - Review
Choosing the right wallet for your cryptocurrency is crucial for its security and accessibility. Here are 5 key differences between hardware and software wallets to help you decide:
1. Security
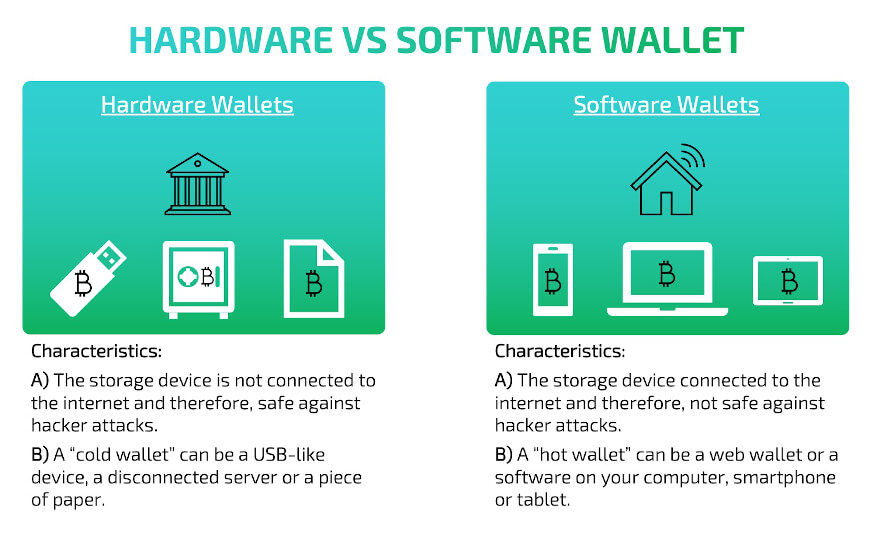
- Hardware Wallet -Considered the most secure option, as your private keys are stored offline on a physical device, isolated from the internet. Hackers cannot access them remotely, even if your computer is compromised.
- Software Wallet -More vulnerable as private keys are stored on your computer or phone, potentially exposed to malware, hacks, or physical loss of the device.
2. Convenience
- Hardware Wallet -Less convenient for frequent transactions. Requires connecting the device to your computer and confirming transactions physically.
- Software Wallet -Highly convenient for everyday use. Transactions can be initiated directly from your phone or computer with a few clicks.
3. Backup And Recovery
- Hardware Wallet -Usually involves a seed phrase for recovery in case of device loss or damage. Losing the seed phrase can result in permanent loss of funds.
- Software Wallet -Recovery options vary depending on the wallet provider. Some offer cloud backups, while others rely on seed phrases. Losing recovery information can lead to lost funds.
4. Cost
- Hardware Wallet -Generally more expensive, ranging from $50 to $200+.
- Software Wallet -Mostly free or have low fees for advanced features.
5. Anonymity
- Hardware Wallet -Some offer more anonymity, allowing transactions without revealing your identity (depending on the specific wallet and service).
- Software Wallet -Anonymity depends on the provider and platform. Some require personal information for verification.
The best choice depends on your individual needs And priorities.
Choose a hardware wallet if
- You prioritize security and hold large amounts of cryptocurrency.
- You are comfortable with a less convenient transaction process
Choose a software wallet if
- You value convenience and make frequent transactions.
- You hold smaller amounts of cryptocurrency and are comfortable with the potential security risks.
What Are Hardware And Software Wallets?
A cold wallet, also known as a hardware crypto wallet, is physical hardware used to store private keys needed to access and use digital assets. Hardware crypto wallets, which resemble USB sticks, have the ability to keep digital assets offline and out of the reach of hackers. However, they must be kept in a secure location to prevent physical harm.
It is possible to combine the most well-known hardware wallets with software wallets to turn hot storage into cold storage. For example, connection with the Trezor cold wallet is made easier by Exodus wallet. Ledger hardware wallets may be integrated with Crypto.com's desktop application.
A software wallet for cryptocurrency, also known as a hot wallet, is a program that can be used on a computer, tablet, smartphone, or other digital device. They are divided into three categories: desktop, mobile, and web wallets, depending on the type of digital device they are being used on. How different software wallets store and handle cryptographic keys is the main distinction between them.
Software wallets can also be divided into custodial and noncustodial categories. While users' digital assets are entirely under their control in noncustodial wallets, custodial wallets are managed by a third party. The drawback is that the owner of a noncustodial wallet forfeits their digital assets if they misplace their keys or passwords.
Examples Of Hardware And Software Wallets
Common Hardware Wallets
1. Ledger
Although Ledgeris most recognized for its hardware wallets, it also offers a specialized desktop app and a well-reviewed mobile app. Smart card encryption, data backup, paperless remote login, PIN entry, and remote password protection are some of the benefits of the Ledger Nano X. Cons: Although Ledger wallets have excellent storage, there is a limit on how much you can interact with decentralized apps (DApps) on them.
2. Trezor
It provides both desktop and high-end gear. It has a smartwatch app even though it doesn't have one for smartphones. Open-source wallets and outstanding seed phrase functionality are two benefits of Trezorwallets. Cons include no smartphone app and restricted support for different browsers and iOS devices.
Common Software Wallets
1. MetaMask
The most widely used DeFi wallet is accessible as an iOS and Android mobile app or browser extension. Both ERC-20 tokens and nonfungible tokens (NFTs) are supported. With its user-friendly wallet UI, MetaMaskgives users complete control over their local money.
2. Trust Wallet
One noncustodial wallet that is well-known for its user-friendly interface is Trust Wallet, which allows users to do a variety of tasks on a single platform. The wallet supports over 100 fiat currencies for cryptocurrency purchases and includes a built-in staking mechanism that lets users stake their cryptocurrency to earn interest.
The lack of direct customer service is one of the disadvantages, though consumers can open tickets for more specialized problems they run into.
3. Electrum
Down tickers at $51,082-only desktop wallet that works with KeepKey, Trezor, and Ledger hardware wallets. Additionally, because it is an open-source program, users can alter the code to add features that meet their needs.Electrummakes up for its limited support for other coins by emphasizing security and transparency. Nevertheless, dependence on documentation is required because there is no direct customer support.
How Do Crypto Wallets Work Under The Hood?
Despite what many people think, your digital assets aren't really stored in a crypto wallet. In actuality, your NFTs and cryptocurrency are kept safe on the blockchain by your wallet. Wallets give you the ability to access your blockchain-stored digital assets. Using the private keys in your cryptocurrency wallet will allow you to access your assets.
A private key is a special combination of characters and numbers that enables you to transfer money and serve as identification for your cryptocurrency wallet. Your recovery phrase, sometimes called the seed phrase, is a phrase of 12 or 24 words that you can use to gain access to your cryptocurrency wallet. It is the human-readable version of your private keys.
To guarantee that your wallet is maintained safe and that only you, the wallet's owner, can access it, you must have your private key. Let's say you unintentionally erase the Trust Wallet app from your phone, which results in the loss of access to it. To get back into your wallet completely, you can use your recovery phrase, which is your private keys.
In reality, all you have to do to receive cryptocurrency is reveal the address of your cryptocurrency wallet if you are using a wallet such as Trust Wallet. In order to send cryptocurrency to someone, you need their wallet address and enough cryptocurrency to cover the transaction fees charged by the blockchain network you are using.
Transactions are facilitated using your wallet's public key, which is generated from your wallet's matching private key. But rather than your public key directly, individuals can send money to your wallet address.
FAQ's About Hardware Wallet Vs Software Wallet
Why Is Hardware Wallet Better Than Software Wallet?
High-Level Encryption - Hardware wallets protect your valuables with robust encryption methods that are very difficult to crack. Sturdy Backup and Recovery: Most of these wallets provide several backup choices, so you can recover your assets in the event that the device is misplaced or breaks.
Are Software Crypto Wallets Safe?
Using a software wallet carries the worst risk because it usually saves your private key in the data store of your browser, albeit encrypted. But since your browser is constantly linked to the internet, this means that your private keys are vulnerable to Internet attacks.
Are Hardware Wallets Worth It?
A hardware wallet is favored by many cryptocurrency owners who possess a variety of assets or substantial sums of them due to its additional offline protection layer. While a hardware wallet is not necessary for users to start investing in cryptocurrencies, it is strongly advised if they are trading substantial amounts of money.
Conclusion
Cryptocurrency wallets are crucial to the Web3 economy. But with so many different cryptocurrency wallets on the market, it's critical to pick one that suits your requirements. Compared to hardware wallets, software wallets are far more widely used and accessible.
This is so that you may use a software wallet right away; all you have to do is download and install it on your smartphone. Hardware wallets, however, must be bought from a reputable vendor and are frequently not inexpensive. Although hardware wallets offer an extra degree of security, they are more difficult to operate and are not suitable for regular cryptocurrency transactions.

Tyreece Bauer
Author
A trendsetter in the world of digital nomad living, Tyreece Bauer excels in Travel and Cybersecurity. He holds a Bachelor's degree in Computer Science from MIT (Massachusetts Institute of Technology) and is a certified Cybersecurity professional.
As a Digital Nomad, he combines his passion for exploring new destinations with his expertise in ensuring digital security on the go. Tyreece's background includes extensive experience in travel technology, data privacy, and risk management in the travel industry.
He is known for his innovative approach to securing digital systems and protecting sensitive information for travelers and travel companies alike. Tyreece's expertise in cybersecurity for mobile apps, IoT devices, and remote work environments makes him a trusted advisor in the digital nomad community.
Tyreece enjoys documenting his adventures, sharing insights on staying secure while traveling and contributing to the digital nomad lifestyle community.

Anderson Patterson
Reviewer
Anderson Patterson, a tech enthusiast with a degree in Computer Science from Stanford University, has over 5 years of experience in this industry.
Anderson's articles are known for their informative style, providing insights into the latest tech trends, scientific discoveries, and entertainment news.
Anderson Patterson's hobbies include exploring Crypto, photography, hiking, and reading.
Anderson Patterson's hobbies include exploring Crypto, photography, hiking, and reading.
In the Crypto niche, Anderson actively researches and analyzes cryptocurrency trends, writes informative articles about blockchain technology, and engages with different communities to stay updated on the latest developments and opportunities.
Latest Articles
Popular Articles