Vault Agent - Empowering Secure Secrets Management
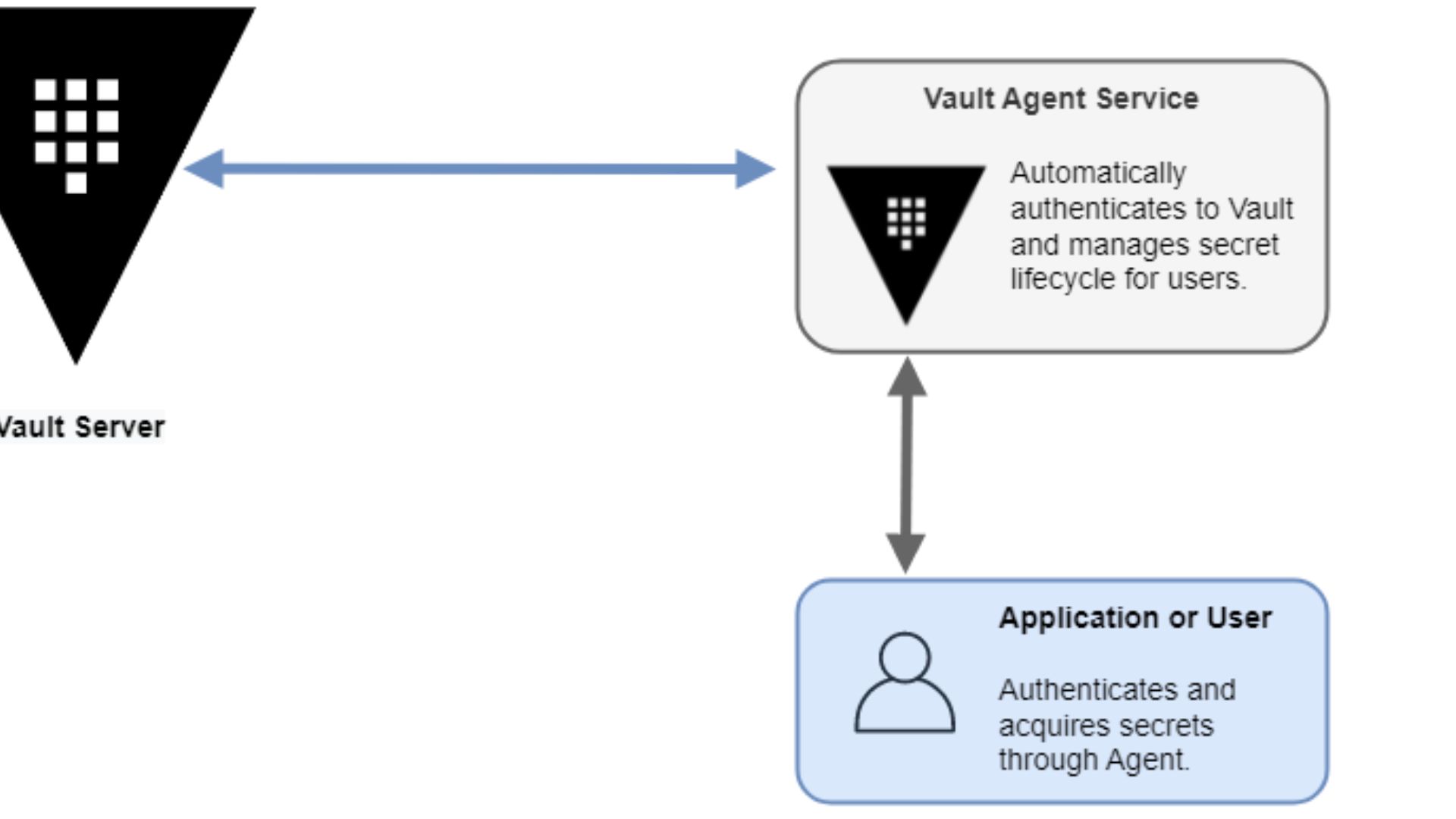
To enhance the usability and flexibility of Vault, HashiCorp introduced Vault Agent, a lightweight daemon that handles the process of securely retrieving and renewing secrets from Vault, relieving developers and administrators from the burden of manual secret management.
Author:Gordon DickersonReviewer:Darren McphersonJun 22, 202370.3K Shares1.4M Views
Securing sensitive information and managing secrets is of utmost importance for organizations. Traditional approaches to secrets management often involve storing credentials and sensitive data in various configuration files, databases, or environment variables, which can lead to security vulnerabilities.
To address these challenges, HashiCorp developed Vault, a powerful open-source tool for secure secret management. Vault provides robust secret storage, encryption, and access control mechanisms.
To enhance the usability and flexibility of Vault, HashiCorp introducedVault Agent, a lightweight daemon that handles the process of securely retrieving and renewing secrets from Vault, relieving developers and administrators from the burden of manual secret management.
What Is A Vault Agent?
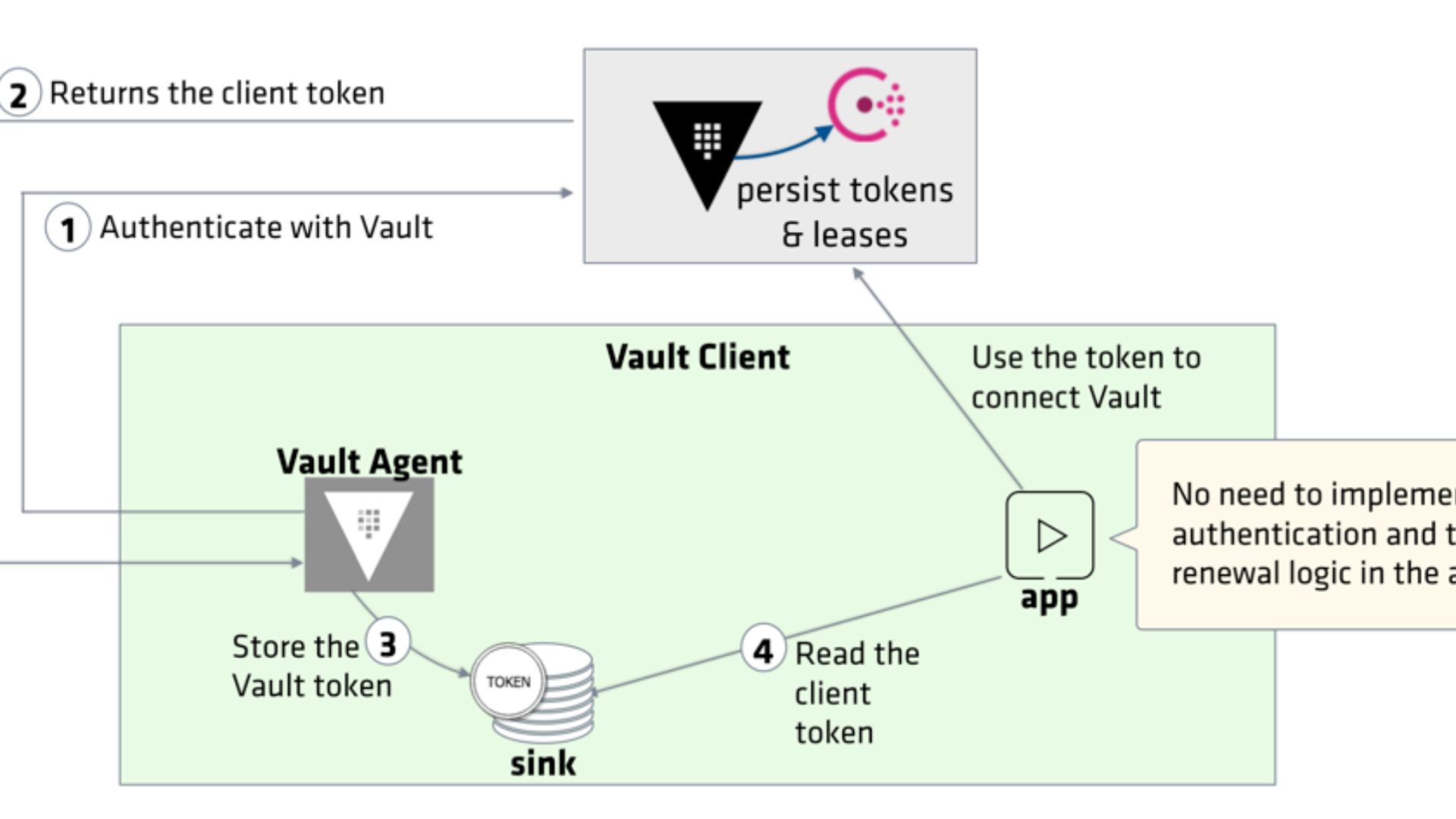
This implies that in addition to using the API to get secrets from Vault, the client application must also use it to maintain the obtained token and perform authentication with Vault. This calls for more testing and application maintenance, as well as code modifications to client apps.
Making (and sustaining) these modifications to apps may not be an issue for certain Vault installations, and it may even be recommended. This may be used in situations where you just have a few apps or when you wish to maintain tight, individualized control over how each application communicates with the vault.
To update and maintain the Vault integration code for every application, you may not have the resources or knowledge to do so in other circumstances where you have a lot of apps, such as in big companies. It is not permitted to include the Vault integration code while the application is deploying third-party apps.
By offering a more scalable and straightforward method for apps to interact with Vault, Vault Agent seeks to lower this first barrier to adoption.
By utilizing Vault Agent, developers can focus on building secure applications without the need to directly interact with the Vault API or handle the intricacies of secret management. Vault Agent offers a seamless way to fetch secrets on behalf of applications, ensuring they always have access to up-to-date credentials and sensitive information.
Key Features Of Vault Agent
Vault Agent comes with a range of powerful features that facilitate secure secrets management. Some of the notable features include:
Automatic Secret Renewal
Vault Agent automatically renews secrets before they expire, eliminating the need for manual intervention. This ensures that applications always have access to up-to-date secrets without disruptions.
Local Secret Caching
Vault Agent caches secrets locally, reducing the number of requests made to the Vault server and minimizing the impact on performance. Cached secrets can be used offline, enhancing the availability and resilience of applications.
Response Wrapping
Vault Agent supports response wrapping, which enables developers to securely transfer sensitive data between different components of an application. This feature adds an extra layer of protection and allows for secure communication within the application infrastructure.
Automatic Token Management
Vault Agent manages the lifecycle of tokens used for authentication with the Vault server. It automatically renews tokens, revokes them when necessary, and handles token rotation seamlessly.
Templated Secret Files
With Vault Agent, it is possible to dynamically generate secret files based on templates. This feature is particularly useful for configuration files or scenarios where secrets need to be injected into specific formats or structures.
High Availability Support
Vault Agent is designed to work in high availability (HA) environments, providing redundancy and failover capabilities. It can seamlessly switch between active and standby Vault servers, ensuring uninterrupted access to secrets.
Getting Started With Vault Agent
To start using Vault Agent, you first need to install and configure Vault and have a running Vault server. Please refer to the official Vault documentation for detailed instructions on setting up Vault.
Once you have a functional Vault environment, follow these steps to get started with Vault Agent:
- Install Vault Agent- Vault Agent can be installed alongside the Vault binary or as a standalone binary. Refer to the official HashiCorp downloads page for the installation package suitable for your operating system.
- Configure Vault Agent - Create a configuration file for Vault Agent. This file specifies the behavior of Vault Agent, including the secret paths to fetch, authentication methods, caching options, and more. We will explore the configuration options in detail in the next section.
- Start Vault Agent- Launch Vault Agent using the configuration file created in the previous step. Vault Agent will establish a connection with the Vault server and begin managing secrets on behalf of your applications.
With the basic setup complete, let's dive into the various configuration options available for Vault Agent.
Configuration
Vault Agent's behavior is defined through a configuration file written in HCL (HashiCorp Configuration Language). The configuration file consists of different sections, each responsible for a specific aspect of Vault Agent's operation. Here are some key sections commonly used in the configuration file:
`auto_auth` Section
This section defines the authentication method for Vault Agent to access the Vault server. It specifies the authentication type (e.g., token, AppRole, Kubernetes, etc.) and the necessary configuration parameters.
Here's an example configuration for using a token-based authentication method:
auto_auth {
method "token" {
mount_path = "auth/token"
config = {
token = "my_vault_token"
}
}
}
`template` Section
The template section is used to configure dynamic secret files based on templates. It specifies the source and destination paths, along with any required transformations or rendering options.
Here's an example configuration for generating a configuration file with a secret injected:
template {
source = "/path/to/template.tpl"
destination = "/etc/myapp/config.yml"
options = {
env = true
}
}
`cache` Section
The cache section defines the caching behavior of Vault Agent. It allows you to control the duration of caching, the maximum number of items to cache, and other cache-related options.
Here's an example configuration for enabling local caching:
cache {
use_auto_auth_token = true
enable_disk_cache = true
}
Below is a table summarizing various configuration options available for Vault Agent:
| Configuration Option | Description |
| auto_auth | Defines the authentication method and configuration parameters for Vault Agent's access to the server. |
| template | Configures dynamic secret files based on templates, specifying the source, destination, and options. |
| cache | Manages the caching behavior of Vault Agent, including disk caching and auto-auth token usage. |
| listener | Configures the network listener for Vault Agent, specifying the address, port, and TLS settings. |
| pid_file | Specifies the file path for storing the process ID of the running Vault Agent. |
| retry | Controls the retry behavior for failed requests to the Vault server. |
| vault | Configures the connection settings and API endpoint for Vault Agent to communicate with the server. |
| vault_api | Defines the API endpoint and related options for Vault Agent to interact with the Vault server. |
| vault_agent_api | Configures the internal API endpoint for Vault Agent communication and coordination. |
| vault_agent_auto_auth | Enables automatic authentication for Vault Agent. |
| vault_agent_cache | Configures the caching behavior for Vault Agent, including the maximum number of items to cache. |
| vault_agent_cache_size | Sets the maximum cache size for Vault Agent, controlling the number of cached items. |
| vault_agent_listener | Defines the network listener settings for Vault Agent, including the address and port. |
| vault_agent_token_file | Specifies the file path for storing the token used by Vault Agent for authentication. |
Vault Agent Usage
Once you have the configuration file ready, you can start Vault Agent using the following command:
vault agent -config=path/to/config.hcl
Vault Agent will read the configuration file and initiate the necessary processes to manage secrets. By default, Vault Agent runs in the foreground, and you can see the logs and activities directly in the terminal.
To run Vault Agent as a background service or daemon, you can use platform-specific mechanisms like systemd on Linux or launchd on macOS.
Integrating Vault Agent
Integrating Vault Agent into your applications and infrastructure is straightforward. Once Vault Agent is up and running, you need to update your application or environment configurations to utilize the secrets managed by Vault Agent.
The process involves replacing the static credentials or sensitive information in your application with placeholders or references. These placeholders are typically environment variables or specific syntax understood by the framework or library you are using.
For example, if your application previously had a configuration file with hardcoded credentials:
database:
host: localhost
username: myuser
password: mypassword
You would update it to use placeholders or environment variables:
database:
host: ${DATABASE_HOST}
username: ${DATABASE_USERNAME}
password: ${DATABASE_PASSWORD}
Then, configure your application or infrastructure to populate these placeholders with the values fetched from Vault Agent. This step varies depending on the platform, framework, or language you are using. Vault Agent provides various options, such as environment variable injection, template rendering, and more, to facilitate this integration process.
By following this approach, your application or infrastructure can dynamically retrieve and use secrets managed by Vault Agent without exposing them directly.
Advanced Use Cases
Vault Agent offers advanced capabilities to address various secret management scenarios. Some notable advanced use cases include:
Dynamic Database Credentials
Vault Agent can generate dynamic database credentials on-the-fly. Instead of using static database credentials, your application can request Vault Agent to create temporary database credentials with a specific TTL (time-to-live). This approach enhances security by minimizing the exposure of long-lived credentials.
Renewing Long-lived Tokens
If your application relies on long-lived tokens for authentication, Vault Agent can automatically renew these tokens on behalf of the application. This ensures uninterrupted access to Vault and eliminates the need for manual token renewal.
AWS EC2 Instance Identity Documents
Vault Agent can fetch and expose AWS EC2 instance identity documents as secrets. This feature simplifies the process of accessing EC2 instance metadata, making it easier to integrate with other AWS services or retrieve valuable information about the instance.
These are just a few examples of the advanced use cases that Vault Agent can handle. The flexibility and extensibility of Vault Agent make it a powerful tool for managing secrets in a wide range of scenarios.
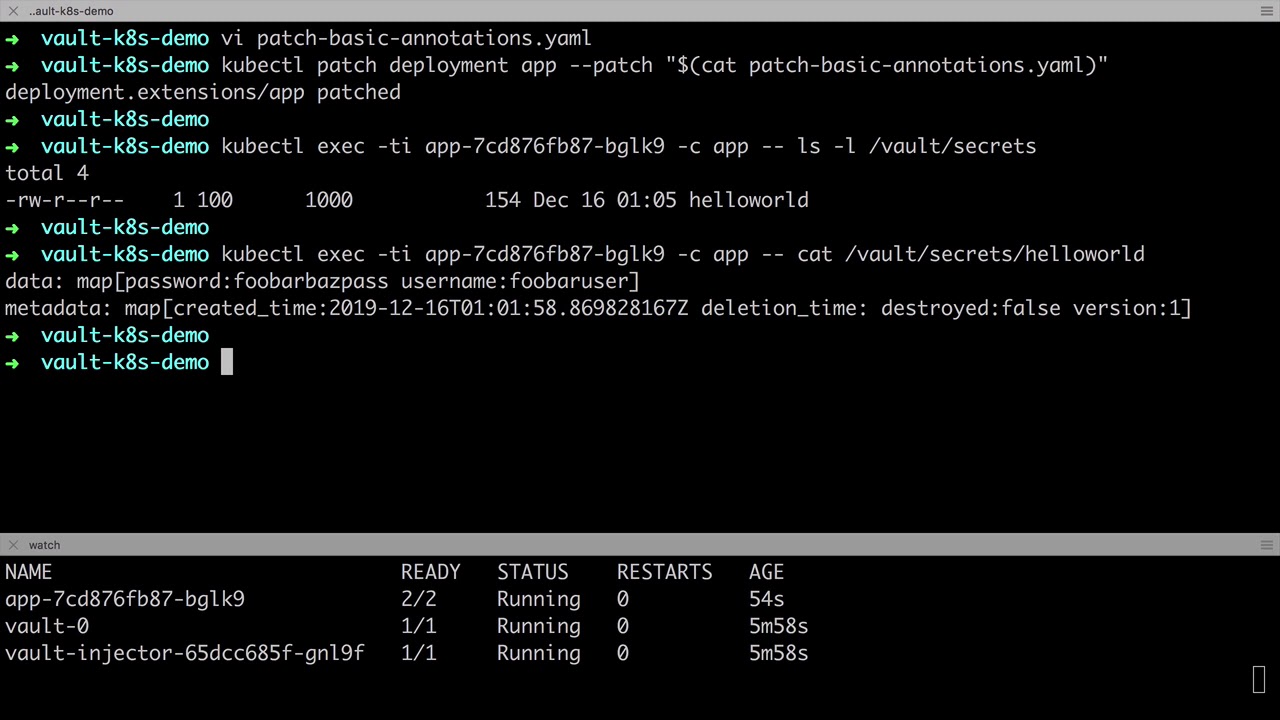
Demo: Vault + Kubernetes Sidecar Injection
Monitoring And Logging
Monitoring Vault Agent is essential to ensure its proper functioning and identify any potential issues or performance bottlenecks. Vault Agent provides several mechanisms for monitoring and logging its activities.
Logging
Vault Agent logs its activities to standard output (stdout) by default. You can redirect the logs to a file or a centralized logging system using standard output redirection or logging aggregation tools like syslog or Fluentd.
Metrics
Vault Agent supports emitting metrics in various formats, including StatsD, Graphite, and Prometheus. These metrics can be collected and visualized using monitoring systems like Prometheus and Grafana, allowing you to gain insights into Vault Agent's performance and behavior.
Enabling metrics requires additional configuration in the Vault Agent configuration file, specifying the metric format, destination, and other related options.
Best Practices
To make the most out of Vault Agent and ensure a secure and efficient secrets management process, consider the following best practices:
- Least Privilege- When configuring Vault Agent, ensure that it has the minimum required permissions and accesses only the necessary secrets. Follow the principle of least privilege to limit the potential impact of any compromised components.
- Monitor and Rotate Tokens - Regularly monitor the lifecycle of tokens used by Vault Agent and rotate them periodically. This practice helps maintain the security of your Vault environment and prevents unauthorized access.
- Protect Configuration Files- Vault Agent configuration files may contain sensitive information, such as authentication credentials. Apply appropriate file permissions and encryption to safeguard these files from unauthorized access.
- Use Dynamic Secrets- Leverage Vault Agent's capability to generate dynamic secrets instead of relying on long-lived credentials. Dynamic secrets have a shorter lifespan, reducing the risk of exposure and enhancing security.
- Enable Audit Logging - Configure Vault Agent and the Vault server to enable audit logging. Audit logs provide an essential trail of activities and can aid in security investigations and compliance requirements.
- Regularly Update Vault and Vault Agent- Stay up to date with the latest versions of Vault and Vault Agent to benefit from bug fixes, performance improvements, and new features. Keeping your software stack updated helps ensure a secure and reliable secrets management infrastructure.
People Also Ask
Can Vault Agent Retrieve Secrets From External Storage Systems?
Yes, Vault Agent can retrieve secrets from external storage systems by configuring appropriate secret backends in the Vault server.
How Does Vault Agent Handle Secret Expiration And Renewal?
Vault Agent automatically renews secrets before they expire, ensuring that applications always have access to up-to-date secret information.
Is It Possible To Monitor The Activity And Performance Of Vault Agent?
Yes, Vault Agent supports logging and metric emission, allowing you to monitor its activities and performance using various logging and monitoring systems.
Can Vault Agent Be Used In A High Availability (HA) Setup?
Yes, Vault Agent is designed to work in high-availability environments and can seamlessly switch between active and standby Vault servers.
What Are The Benefits Of Using Vault Agent For Secrets Management?
Vault Agent simplifies secrets management by automating the retrieval, renewal, and caching of secrets, reducing manual effort and enhancing security.
Conclusion
Vault Agent is a powerful tool that simplifies secure secrets management by automating the retrieval, renewal, and caching of secrets from HashiCorp Vault. With its range of features and flexible configuration options, Vault Agent empowers developers and administrators to build secure applications without the complexities of manual secret management.
By adopting Vault Agent, you can enhance the security, scalability, and maintainability of your secrets management process. Embrace the power of Vault Agent and unlock the potential of secure secrets management in your organization.

Gordon Dickerson
Author
Gordon Dickerson, a visionary in Crypto, NFT, and Web3, brings over 10 years of expertise in blockchain technology.
With a Bachelor's in Computer Science from MIT and a Master's from Stanford, Gordon's strategic leadership has been instrumental in shaping global blockchain adoption. His commitment to inclusivity fosters a diverse ecosystem.
In his spare time, Gordon enjoys gourmet cooking, cycling, stargazing as an amateur astronomer, and exploring non-fiction literature.
His blend of expertise, credibility, and genuine passion for innovation makes him a trusted authority in decentralized technologies, driving impactful change with a personal touch.

Darren Mcpherson
Reviewer
Darren Mcpherson brings over 9 years of experience in politics, business, investing, and banking to his writing. He holds degrees in Economics from Harvard University and Political Science from Stanford University, with certifications in Financial Management.
Renowned for his insightful analyses and strategic awareness, Darren has contributed to reputable publications and served in advisory roles for influential entities.
Outside the boardroom, Darren enjoys playing chess, collecting rare books, attending technology conferences, and mentoring young professionals.
His dedication to excellence and understanding of global finance and governance make him a trusted and authoritative voice in his field.
Latest Articles
Popular Articles